In a recent cyber assault that has sent shockwaves through the U.S. aerospace sector, a sophisticated spearphishing attack orchestrated by the threat actor AeroBlade has revealed alarming vulnerabilities. This incident underscores the pressing need for enhanced cybersecurity measures in critical infrastructure industries, especially within aerospace, to counter evolving threats.
Lessons Unlearned in Critical Industries
Roger Grimes, a data-driven defense evangelist at KnowBe4, underscores the necessity of four crucial steps to thwart such attacks: anti-social engineering training, consistent patching, phishing-resistant multifactor authentication, and robust password policies. Grimes asserts, “If the aerospace industry took just those four steps, threats such as AeroBlade would not see continued success.” This breach highlights the significance of proactive cybersecurity measures for safeguarding critical industries against persistent threats.
Unraveling the AeroBlade Spearphishing Attack
The BlackBerry Threat Research and Intelligence team dissected the attack, revealing that AeroBlade’s spearphishing strategy involved a weaponized document named [redacted].docx, utilizing a remote template injection technique and malicious VBA macro code. Operational since September 2022, the attack entered the offensive phase in July 2023, showcasing a sophisticated and strategically planned assault uncommon in typical cyberattacks.
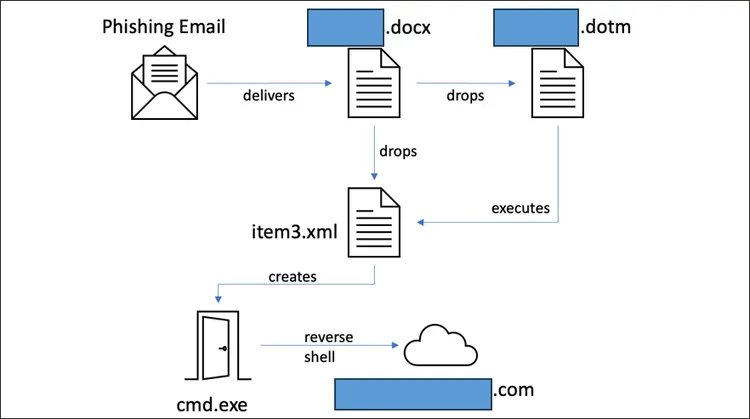
The Sophistication Behind the Spearphishing Campaign
Callie Guenther, senior manager of cyber threat research at Critical Start, emphasized the attack’s sophistication. The year-long gap and the use of a remote template injection technique indicated a high level of commitment, suggesting involvement from state-sponsored or highly organized criminal groups. Guenther explained that this technique cleverly bypassed security measures, granting the attacker control over the victim’s system and exhibiting meticulous reconnaissance capabilities.
The Patient Adversary: Understanding the Threat Actor
Donovan Tindill, director of OT cybersecurity at DeNexus, noted the threat actor’s patience, spending nine months in a testing phase before escalating the offensive attack. While BlackBerry expresses “high confidence” in identifying commercial cyber espionage, Tindill warns that there’s no guarantee the threat actor won’t escalate to ransomware or data encryption in the future. Anurag Gurtu, CPO at StrikeReady, stressed the seriousness of the AeroBlade attack due to the sensitive nature of aerospace company data, urging organizations to strengthen cybersecurity defenses and prioritize employee training.
Strengthening Defenses for Future Resilience
The AeroBlade spearphishing attack serves as a stark reminder of the evolving and sophisticated nature of cyber threats targeting critical industries. As the aerospace sector faces increasing risks, adopting comprehensive cybersecurity measures and investing in employee training are imperative to mitigate potential breaches and safeguard sensitive information. Organizations must remain vigilant and proactive to ensure the resilience of their defenses against ever-evolving cyber threats.
Related Articles
AI-Powered Phishing Scams on the Rise in 2023
AI-Powered Phishing Scams on the Rise in 2023 As the holiday season brings joy and festivities, it also marks a concerning surge in cyber threats. In 2023, holiday phishing scams have taken a sinister turn, with cybercriminals leveraging generative artificial...
Apple’s Alarming Data Breach Report Unveils 2.6 Billion Records Compromised Over Two Years
Apple's Alarming Data Breach Report Unveils 2.6 Billion Records Compromised Over Two Years Apple-commissioned data breach report, led by MIT Professor Stuart Madnick, has exposed a staggering 2.6 billion records pilfered by hackers between 2021 and 2022. Released on...
Data Breach at 23andMe Exposes 7 Million Users
Data Breach at 23andMe Exposes 7 Million Users 23andMe, a prominent DNA testing and ancestry service, has confirmed a significant data breach affecting nearly 7 million of its customers. The breach, which occurred in October, exposed sensitive health-related...

